Top 10 Intrusion Prevention System
Snort IPS uses a series of rules that help define malicious network activity and uses those rules to find packets that match against them and generates alerts for users. An Intrusion Prevention System IPS goes a step further by inspecting each packet as it traverses a network interface to determine if the packet is suspicious in some way.

Top 10 Best Intrusion Detection Systems Ids 2022 Rankings
Breach prevention and advanced security capabilities including an intrusion prevention system IPS URL filtering sandboxing state-of-the-art malware protection and advanced threat.

. Intrusion prevention systems are thereby used to examine network traffic flows in order to find malicious software and to prevent vulnerability. To block these an intrusion prevention system is required. Its main function is to raise an alert when it discovers any such activity and hence it is called a passive monitoring system.
A typical IPS configuration uses web application firewalls and traffic filtering solutions to secure applications. An IPS is an IDS with built-in workflows that are. Zeek can be deployed in conjunction with Dynamite-NSM a free Network Security Monitor to expand its capabilities and to take advantage of their advanced graphical displays of log data.
This makes Bro an intrusion prevention system. Cloud Mitigation Provider Cloud mitigation providers are experts at providing DDoS mitigation from the cloud. If it matches a known pattern the system can drop the packet in an attempt to mitigate a threat.
An IDS is an intrusion detection system and an IPS is an intrusion prevention system. There are six basic approaches to Intrusion Detection and Prevention. The intrusion detection software can be installed on Unix Linux and Mac OS.
SP 1800-10 Protecting Information and System Integrity in Industrial Control System Environments. Snort has three primary uses. Firewalls intrusion detection systems malware scanners integrity auditing procedures and local storage encryption tools can each serve to protect your information technology resources in ways.
Some of these methods are implemented inside. Snort can be deployed inline to stop these packets as well. SP 1800-9 Draft Access Rights Management.
Snort is the foremost Open Source Intrusion Prevention System IPS in the world. It is device or software application that monitors network or systems for malicious activity or policy violations. As a packet sniffer like tcpdump as a.
Access Rights Management for the Financial Services Sector. Prevention Given that Denial of Service DoS attacks are becoming more frequent it is a good time to review the basics and how we can fight back. Cybersecurity for the Manufacturing Sector.
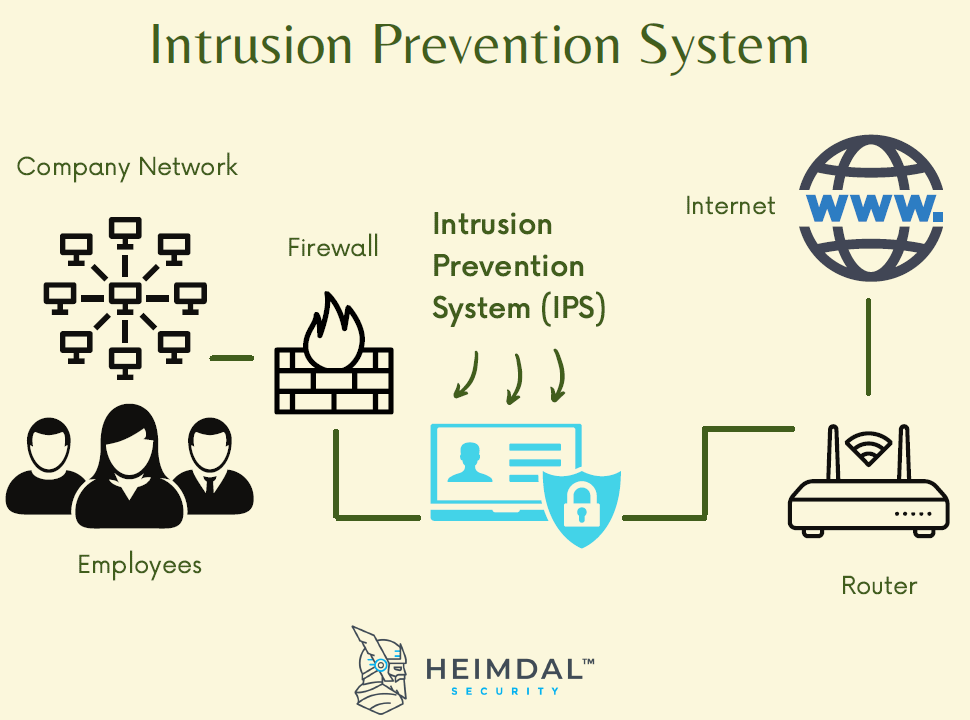
The idea behind intrusion prevention is to create a preemptive approach to network security so potential threats can be identified and responded to swiftly. An intrusion prevention system IPS is a network security and threat prevention tool. An Intrusion Detection System IDS monitors all incoming and outgoing network activity and identifies any signs of intrusion in your system that could compromise your systems.
While an IDS works to detect unauthorized access to network and host resources an IPS does all of that plus implements automated responses to lock the intruder out and protect systems from hijacking or data from theft. What is an intrusion prevention system IPS An IPS complements an IDS configuration by proactively inspecting a systems incoming traffic to weed out malicious requests. An Intrusion Prevention System IPS is a step ahead of IDS with.
Intrusion Detection System IDS Intrusion Prevention System IPS IDS stands for Intrusion Detection System IDS. Choosing an interface You can. The Suricata software can operate as both an IDS and IPS system.

Top 10 Intrusion Detection And Prevention Systems Clearnetwork Inc

No comments for "Top 10 Intrusion Prevention System"
Post a Comment